The AppSec Remediation Agent
Seal Security’s AppSec Remediation Agent delivers real, human-vetted, production-ready fixes for open source vulnerabilities - resolving risk directly in your applications without slowing teams down.

%20(1).avif)
Why security and engineering teams trust us


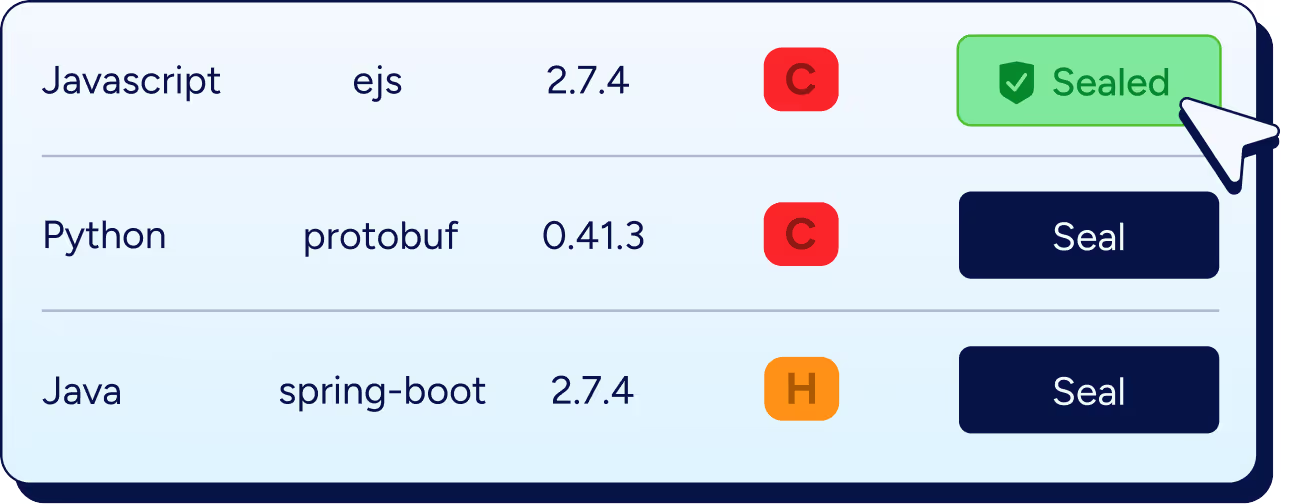
How do you Seal open source vulnerabilities?
- Integrate Seal with your build pipelines, or directly to your artifact server.
- During build, Seal swaps all known vulnerable libraries with their Sealed counterparts, according to the pre-approved organization policy.
- From there, your release process stays the same: build, test, and deploy.
- Finally, Seal helps ensure all projects stay up to date with the latest security patches to prevent drift.
Autonomous remediation. Human-approved.
Always in your control - every fix is visible, reviewable, and approved by your team.
Remediation you can ship with confidence

No upgrade required
Don’t get forced into risky upgrades just to address a CVE in a transitive dependency. Patch now, upgrade on your own timeline.
Fix the “unfixable”
Secure transitive dependencies, EOL libraries, and legacy systems that scanners mark as "no fix available".

Compliance ready, always
Patches are human-readable, so you can review before applying. Stay continuously compliant with 72-hour remediation SLAs.

One command is all it takes
Run a single CLI command after resolving your dependencies - no manifest files touched, no dependency conflicts.
Reviewed by humans, tested by machines, validated by AI
Each patch goes through expert security review, extensive automated testing, and Seal’s AI validation to guarantee build safety.

No vendor lock-in
Sealed libraries remain in your registry indefinitely. Even if you stop using Seal.

Fix open source vulnerabilities across your stack with one unified solution

Secure application dependencies
Patch direct and transitive dependencies in place, even the ones your scanner marks as “unfixable”.
Uphold compliance and meet customer SLAs
Pass every scan and meet every SLA for FedRAMP, PCI DSS 4.0, NYDFS, and customer audits.
Secure end-of-life environments
Keep CentOS, RHEL 6, and other EOL distros secure with post-EOL security patches.

Secure legacy and hard-to-manage code
Fix vulnerabilities in legacy apps and vendor-supplied software, even without source code access.

Secure your entire Linux infrastructure
Deploy backported fixes across containers, VMs, and bare metal without breaking upgrading your OS.
Latest research and publications
Frequently asked questions
Discover how Seal Security identifies and patches open source vulnerabilities without breaking changes.
Seal Security delivers one-click, backported, fully compatible patches for existing versions of open source packages. Seal identifies and fixes vulnerabilities across your entire stack, from application dependencies, to Linux packages within your containers in your production environments, to post-EOL bare metal devices. Seal’s approach reduces technical debt, prevents risk downtime, and helps teams ship faster, without breaking changes or compromising security and compliance posture.
Seal Security handles all critical and high rated vulnerabilities within 72 hours of being made public.
Seal Security streamlines audit-readiness and continuous compliance for FedRAMP, PCI DSS 4.0, NYDFS, HITRUST and DORA.
Seal Security supports all major programming languages - including Java, Python, JavaScript, C/C++, Go, PHP, C#, and Ruby - across a wide range of package managers such as Maven, Gradle, PyPI, Poetry, npm, pnpm, Yarn, yum, dnf, apt, apk, Composer, NuGet, and Bundler.
Seal Security integrates with GitHub, GitLab, and Azure DevOps. It also supports major SCA tools, like Snyk, BlackDuck, GitHub Advanced Security, Checkmarx, Ox, alongside vulnerability scanners such as Wiz, Trivy, StackRox, and Grype to automate remediation within your existing workflow.
Seal Security supports all major Linux distributions, including Red Hat Enterprise Linux (RHEL), CentOS, Alpine Linux, Debian, Ubuntu, and Oracle Linux.
Seal Security is certified with SOC 2 Type II and ISO 27001.















.jpeg)