Eliminating Protestware Risks with Seal Security: Ensuring Secure Library Usage

Introduction:
Software vulnerabilities pose a significant threat to organizations of all sizes. To address these risks, companies typically rely on timely updates and patches for third-party libraries. However, a new challenge has emerged in the form of protestware – software intentionally manipulated to convey messages, potentially causing unintended consequences or harm.
In this blog post, we explore the potential risks of protestware and demonstrate how Seal Security's unique approach mitigates these threats by providing sealed versions of libraries that are both secure and protestware-free.
Understanding protestware:
Protestware is a type of software or code library that developers modify to raise awareness or convey messages about contentious issues. Unlike regular software, protestware introduces unexpected actions, which can range from benign displays of messages or images to more damaging effects like restricting access, altering functionality, or even erasing user data. As a result, organizations relying solely on traditional library updates are vulnerable to potential protestware attacks.
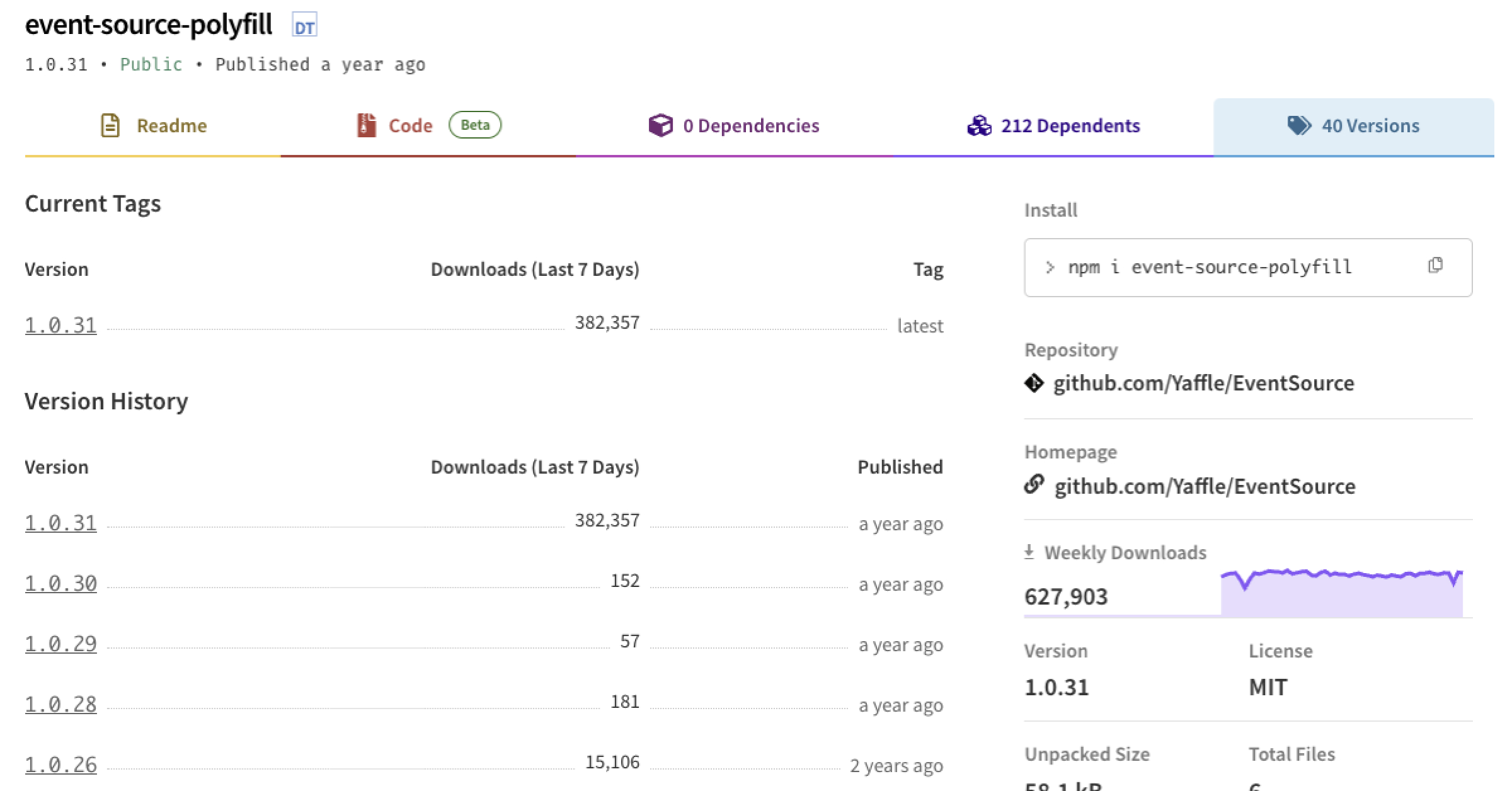
event-source-polyfill
Polyfill packages are designed to implement existing JavaScript features on web browsers that may not support them. As such, the package in question expands Mozilla's 'EventSource' APIs to other browsers that may lack the concept. On March 17th 2022, Russian developer based from Netherlands added a peculiar piece of code to version 1.0.26 his popular npm library event-source-polyfill.
This update includes a pro-Ukrainian message that appears 15 seconds after the library loads, but only if the browser's timezone is set to Russia. After showing the alert, the browser attempts to open http://www.change.org/NetVoyne using a window.open call, which sparked an intense discussion on GitHub.
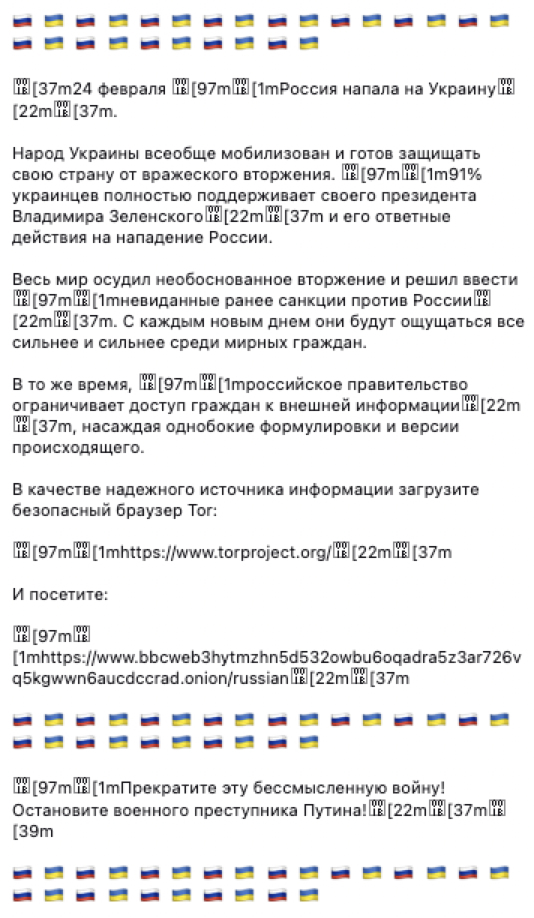
Any user performing periodic updates of their libraries would have received the version containing the undesired behavior. Since it's triggered only under specific circumstances it would be extremely hard to detect, either by automated or manual testing. Moreover, the issue was not recognized as a security issue, so almost none of the SCA tools inform the users they are using a problematic version.
The undesired code was removed in version 1.0.29 released on August 11th 2022, nearly 5 months later. Nevertheless, even now, more than a year and a half later, according to npm there are 15k weekly (2.5% of the total number of) downloads including the undesired behavior.
node-ipc
node-ipc is a nodejs module for local and remote Inter Process Communication with full support for Linux, Mac and Windows. As a dependency, node-ipc is automatically downloaded and incorporated into other libraries, including ones like Vue.js CLI, which has more than 1 million weekly downloads.
On March 7th 2022, the node-ipc author pushed a new version 10.1.1. This package contains malicious code that targets users with IP located in Russia or Belarus, and overwrites their files with a heart emoji. Popular JavaScript front end framework Vue.js also uses node-ipc as a dependency. But prior to this incident, Vue.js did not pin the versions of node-ipc dependency to a safe version and was set up to fetch the latest minor and patch versions instead, as evident from the caret (^) symbol. As such, Vue.js CLI users made an urgent appeal to the project's maintainers to pin the node-ipc dependency to a safe version.
In this specific case, the community responded much faster. The issue was allocated CVE-2022-23812, with score of 9.8 due the the high severity of the undesired behavior. The problematic code was removed a day later on March 8th 2023, and the malicious version was removed from the public npm registry.
colors.js
colors.sj provides color and style in your node.js console. The developer, named Marak Squires added a "new American flag module" to colors.js library in version v1.4.44-liberty-2 that he then pushed to GitHub and npm. Tainted versions 1.4.1, and 1.4.2 also followed on npm.
Users of popular open-source projects, such as Amazon's Cloud Development Kit (aws-cdk) were left stunned seeing their applications print gibberish messages on their console. These messages included the text 'LIBERTY LIBERTY LIBERTY' followed by a sequence of non-ASCII characters:
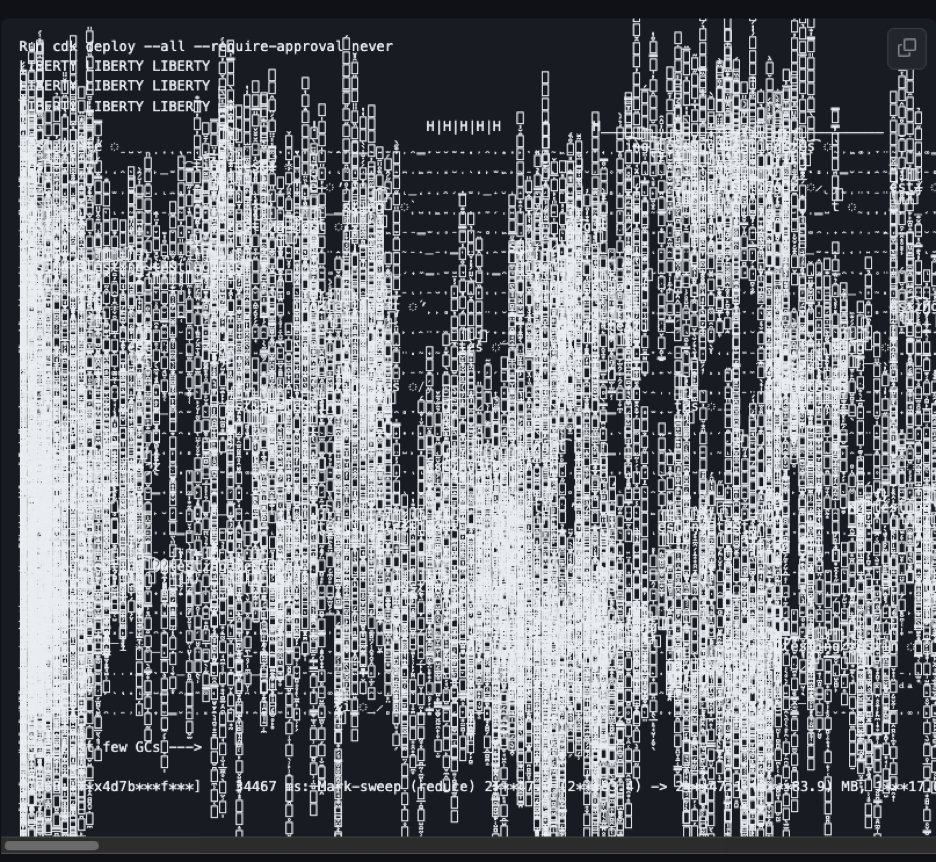
Popular libraries responded to this problem by a more precise version pinning to revert back to 1.4.0. One example is aws-cdk, which released a new minor version 2.5.0 bundling this critical security fix with potentially breaking changes.
Seal Security's Solution:
Seal Security revolutionizes the way organizations address software vulnerabilities by offering sealed versions of third-party libraries. These sealed versions provide a fully compatible and secure alternative, incorporating the necessary security fixes without the risks associated with protestware. By leveraging Seal Security's approach, organizations can ensure a secure software environment while avoiding unintended consequences.
Conclusion:
In an era where software vulnerabilities and protestware threats are on the rise, organizations need a reliable solution to mitigate risks while maintaining a secure software environment. Seal Security's approach offers sealed versions of libraries, providing fully compatible and protestware-free alternatives. By embracing this innovative approach, organizations can confidently remediate vulnerabilities without exposing themselves to the potential consequences of protestware attacks. Protect your software ecosystem with Seal Security and safeguard your organization's integrity and reputation in an increasingly interconnected world.